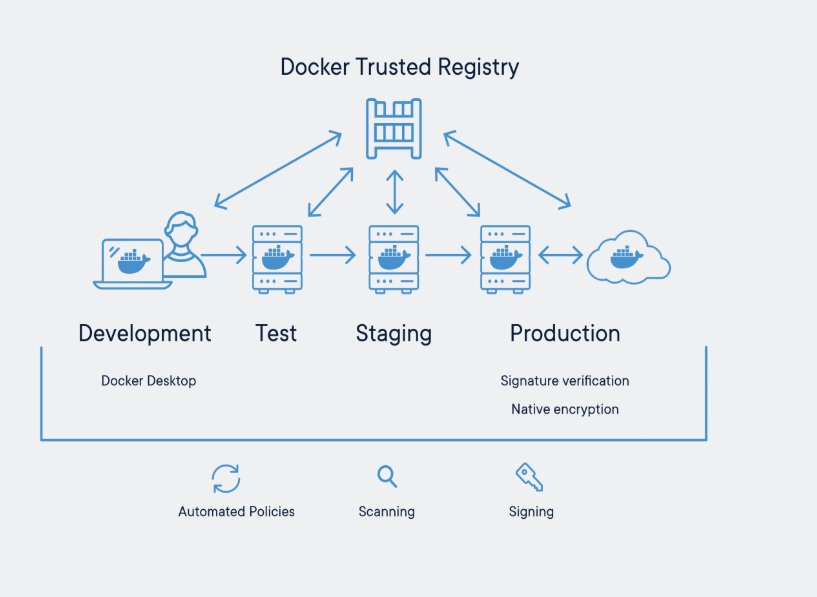
Docker security is becoming very challenging compared to traditional technologies as it requires all-around protection, including application firewalls, host machine protection, and real-time container defense. In our last article, we have covered the docker security vulnerabilities and overview of security measures. In this article, we will elaborate on the security features of dockers.
The four quadrants of docker security:
While the development phase, we need to keep in mind the below four areas while developing container-based applications,
- Securing kernel with support for namespace and cgroups
- Securing Docker daemon
- Security loopholes in the container configuration profile
- Removal and adjustment of capabilities
Kernel Namespace
- Kernel namespace is a Linux feature that isolates the kernel resources among different running containers and processes.
- The processes running within a container have got their own set of resources in an isolated environment.
- This feature allows running multiple Docker containers over a host machine without affecting the host or the other running container resources.
- Kernel namespacing provides network stack isolation, one process running inside a container can not access the network interfaces and sockets of another container.
Control groups
- Contol groups or cgroups is a Linux feature that monitors, limits, and accounts the allocated resources to the running processes.
- From the Dockers point of view, cgroups ensures a fair share of system resources such as memory, disk I/O, CPU among the running containers.
- The limiting feature of cgroups ensures that no single container is allowed to take down the system by exhausting the available resources.
- It effectively defends the Denial-Of-Service(DOS) attack and assures steady up time for the running containers in Platform as a Service(PaaS) cloud model.
Docker Daemon Security
- Docker daemon is the primary service running on the host machine and listens to all the Docker API requests to handle objects such as images, containers, volumes, and networks. When you are running any docker containers, that means docker daemon is running consistently behind the scene and handles everything.
- Docker daemon requires root user privileges, and only trusted users should be allowed to control the daemon.
- Virtualization system file-sharing should be appropriately managed, or else running docker containers can alter the host file system without any restriction.
- When you are deploying restful services to the container, you need to very careful to validate the user inputs as malicious commands might lead to the creation of arbitrary containers.
- Docker daemon started using the UNIX socket instead of TCP ports to secure the dockers’ rest endpoints.
Container configuration profile
- In the past, many security docker security vulnerabilities were reported for the containers running with a default configuration profile. It is always advisable to customize the config file to best suit your security needs.
- Customized docker config files are more vulnerable to container threats; it’s always recommended to read the documentation and understand the source code.
- Following best practices and using the security benchmark tools is recommended.
Capabilities removal
Docker daemon requires a few Linux capabilities to work like a charm. It doesn’t need all the Linux capabilities, and having too many additional capabilities will increase the vulnerable hotspots. In this section, we will how Docker elevated its security level by removing below capabilities in the past,
- CAP_MAC_ADMIN: MAC configuration and permission for the state change.
- CAP_MAC_OVERRIDE: Mandatory Access Control (MAC) override for the Smack LSM.
- CAP_SETPCAP: Root processes can set the capabilities of another process.
- CAP_SYS_NICE: Modify the priority of other processes. Removal of this capability was a big step towards the isolation of containers.
- CAP_SYS_RESOURCE: Override system resources and can affect the cgroups.
- CAP_SYS_TIME: Processes running within the docker containers are not allowed to change the system time of the Linux environment.
- CAP_NET_ADMIN: This capability enables processes to configure the network dynamics of the engine.
- CAP_SYSLOG: As Linux kernel makes use of printk to log the system information, this capability removal was surely a big step.
- CAP_SYS_RAWIO: Kernel memory modification was removed to secure the intentional kernel memory modification within the container.
Conclusion
Docker security is a hot topic of discussion as many organizations started shifting towards containerization-based project deployments. Docker team is working consistently to fill the security loopholes and heading towards complete container isolation.







Leave a Reply