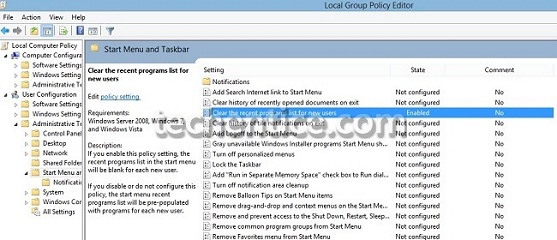
Group Policy is a feature in Windows Operating System which controls the working environments of the user and computer’s accounts properly. It provides the centralised management ad helps in configuring the user’s settings in the operating system in an Active ...
The system files are the most important files that help in the proper functioning of the operating system. If these files are changed it might happen that your computer may not function properly. So it is always advisable not to ...
Today, it’s very easy to share your knowledge to a lot of people. Say thanks to iTunes and iPod. Podcasting has become a very popular way to share information from people around the world. Planning to start your own podcast? ...
Not several years ago, hearing to music was really an costly hobby. You would surely purchase a costly CD or DVD player, and then retain your music array on tape cassettes or optical discs ready at hand at all times ...
The search engine giant Google, rose up with an algorithm called “PageRank’ to place websites on their lookup results. The algorithm was identified so after one of Google’s founders, Larry Page. This was the foremost algorithm which Google had arisen ...
Firefox comes with brawny features to forbid you from being chased online, but they aren’t on by default. We’ll explain you how to take charge of your secrecy online with Firefox’s choices. Firefox as well has few features that transmit ...
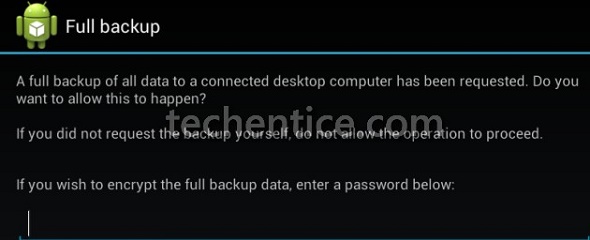
Android comes with a built-in way to back up and restore all your contents of your phone or tablet. All you require is a computer and a device executing Android 4.0 or more newfangled. We’ve also accounted for backing up ...
Web browsers have been developing up over the preceding few years. Now that Internet Explorer 6’s possession on the web has been taken over, browsers have been applying a mixture of cool fresh features that websites are having advantage of ...
“I didn’t have time to write a short letter, so I wrote a long one instead.” Mark Twain It’s always a challenge to create something small yet beautiful. And this is an ordeal that a web designer often faces when ...
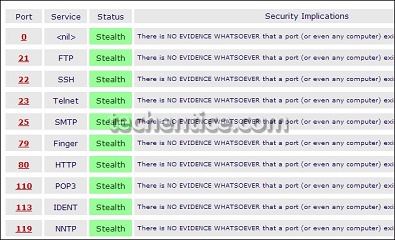
So you possess an antivirus securing your system, your firewall is up, your browser plug-ins are all up-to-date, and you’re not leaving out any security mends. But how can be rest assured your defense mechanisms are really working as well ...
Phishing occurs when someone undertakes to use electronic communication such as email to fraudulently gain private information such as password thereby pretending to be an entruted person or a part of a trusted group. With such private information on the ...
We lately viewed at the several causes you might require to use a third-party DNS server. You can alter the DNS server for your whole network on your router or set it singly on a PC or other device. Shifting ...
Android phones uses an ambient light sensor to mechanically adjust the phone’s brightness. It is up to every Android phone’s maker to correctly fine-tune he auto-brightness characteristic and in general they don’t end up doing an incredible job. The range ...
Whenever we send an e-mail, we cannot undo it if the message is already sent. On sending an e-mail, the mail client sends a copy of the message to the receiver whose e-mail server receives it and shows it in ...
In last couple of years, we have seen the uprising of closed platforms- operating systems that only permit you to install software sanctioned by the operating system.s programmer. Nonetheless, many democratic platforms-even the mobile ones are yet open platforms. Platforms ...
Linux users frequently want to execute Windows software on Linux, but Windows users may want to execute Linux software, too. Whether you’re searching for a enhanced development environment or hefty command-line tools, you can execute Linux software without departing Windows. ...
While several of us gaze at our signal bars, awaiting for the 3G to swop over to 4G, China-based Huawei is rather looking for the next great thing with a goodish $600m investment into 5G research. Don’t turn out too ...
Hackers set onn against Bitcoin wallet Inputs.io and slipped away 4,100 Bitcoins. At present prices for the online substitute currency, that sums upto $1.18 million. Inputs.io barons a Bitcoin billfold service where possessors can easily send out and receive Bitcoin. ...
VPS hosting or Virtual Private Server hosting is one of the most commonly used services by corporations across the world. The main question is: Why not a dedicated web hosting service or a shared web hosting service? Today, we will ...
Months back, Microsoft showed us a vision of how our coming days are going to be through a video giving a flavor of what is called a smart home. Smart Home is a facility of internet connectivity all over home ...