Users are greatly worried about their data privacy and its security and hence they rely on VPNs for the security of their data. But do these VPNs collect your browsing data and sell it to third parties? The main purpose ...
It is, without a doubt, one of the most frustrating feelings known to the modern Mac user. You log on to your computer, ready to dive into some hard work (or aimless social media scrolling), only to have your efforts ...
You hear so many hacking horror stories these days — it’s clearly become more important than ever to keep your home network, and the devices connected to it, safe. Your privacy is at risk, and so is your finances. And ...
2020 has brought with it new tech as far as data recovery is concerned. These innovations have been useful for business. This is primarily because many employees have been working remotely, and hence the risk of data loss has been ...
Your privacy is a right, but it’s not a given. More often than not, people will put their interests first and infringe on your rights to serve their own agenda. For instance, a website you visit may look at your ...
Aptoide is a marketplace for applications that can be downloaded and used on Android devices. Yes, when people think of an alternative to Google Play Store, they switch to Aptoide. Aptoide was launched in the year of 2009 with the ...
In the era of technology and innovations, browsing the IoT (Internet of Things) without proper protection can leave your sensitive data and privacy vulnerable to hackers and common cyber threats. Most households have multiple devices connected to the internet. The ...
The gaming industry has seen great traffic of individuals looking forward to it as a full-time career more recently with the striking increase in demand of Discord. For the same reason, an increased expectation of new and fun content is ...
As technology is advancing daily, so are the cybercrimes because hackers have now started incorporating the latest technical equipment in their malicious activities and have access to the latest technology, which can prove to be very dangerous for internet users. Therefore, you need ...
With more companies switching to a remote environment and constant changes in technology, cybersecurity is more relevant than ever. As an employer, keeping your employees and business safe is an effort that goes beyond the IT team. Whether physically in ...
The term backdoor sounds a little awkward in computer terminology. But you should take note that it can be very dangerous if it is on your computer system or network. Now the question must be about how dangerous it can ...
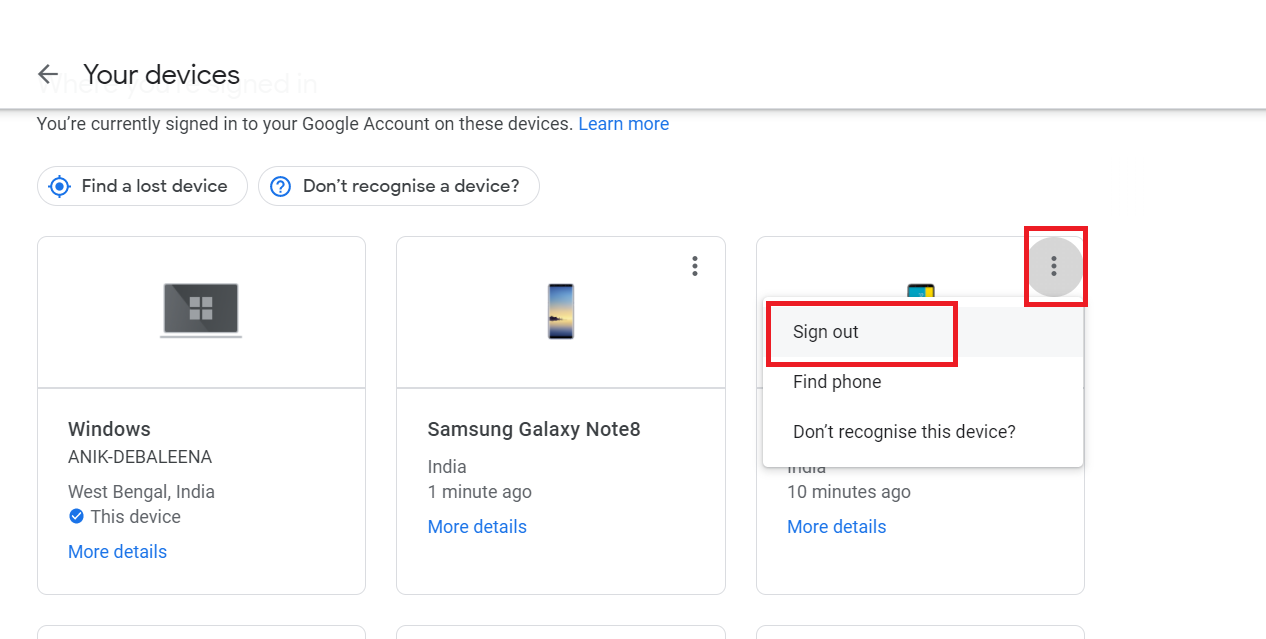
In this article, I shall show you how to remove any device connected to your Google account. This will be helpful in recognizing, which devices still have your Google account signed in. If you have ever signed in to your ...
Fleeceware name should be enough to warn you to stay away. They are dangerous, but cannot be called malware. These apps do not involve installing a virus or anything similar to your computer or any other device like mobile. Nevertheless, ...
Where the internet is surrounded by all kinds of threats, having the best secure router is the need of the time. It is required to secure your home network and all of your computers, gaming consoles, smartphones, and IoT devices ...
A site-to-site (VPN) is a connection amongst two or more networks, such as a corporate network and a branch agency network. Many organizations use site-to-site VPNs to influence an internet connection for private traffic as a substitute to using individual MPLS circuits. Companies ...
Do you know the location of your clients? Can you identify and block suspicious devices and traffic? Are you able to tell whether the clients on your network are all approved to access its information? If ‘no’ is your answer ...
Thunderbolt is a hardware brand interface and a product of Intel. It helps the communication between the computers and external devices. Most companies prefer the use of Thunderbolt interface. It is easy to crack the security of Thunderbolt using Thunderspy ...
Taking it for the past, how tedious transcription used to be. How difficult and sometimes irritating it might have been to jot down points from the notes and conversations recorded on a dictaphone. Well, now, things are different. In the ...
The number of identity theft crimes has been exponentially increasing that involves crimes ranging from credit-card frauds to mishandling security numbers and also full-on impersonation. You need to have the best plans with you to keep yourself safe from identity ...
Unknown numbers, making your phone ring throughout the day are one of the most irritating things everyone has to face. These are the robocalls that make us hyperventilate and get on our nerves are still increasing. Reports say that almost ...